Threatpost Spreads Inaccurate Information on Exploited WordPress Plugin Vulnerability from Palo Alto’s Unit 42
We often incorrectly get referred to as security researchers, something we have never claimed to be. Considering the quality of a lot of security research there might be good reason to avoid that title. One such example we just ran across also provides yet another example of the bad security journalism going on with WordPress plugin vulnerabilities. We thought we would write a quick post about it since we took a few minutes to look into the claims and what we found seems worth noting.
Yesterday we were notified through a Google alert to a Threatpost story “Exploits for Social Warfare WordPress Plugin Reach Critical Mass”, which seemed odd since the main vulnerability, which we discovered, was widely exploited a while ago, so critical mass has likely long since past.
Part of the story made the source for it, Palo Alto’s Unit 42 team, seem questionable:
“There are many exploits in the wild for the Social Warfare plugin and it is likely they will continue to be used maliciously,” the researchers said. “Since over 75 million websites are using WordPress and many of the high traffic WordPress websites are using the Social Warfare plugin, the users of those websites could be exposed to malware, phishing pages or miners.”
What would the number of websites using WordPress matter, since the vulnerability only involves a single plugin? It isn’t like you need to guess how many websites are using WordPress plugins and the figure for Social Warfare is only 60,000, so mentioning the millions figure seems out of place.
The story claims that most of those websites are still vulnerable:
Social Warfare, which allows websites to add social sharing buttons to their pages, is vulnerable in all versions prior to 3.5.3; a patch was issued on March 21 after news of what was then a zero-day emerged. Yet many websites haven’t updated the plugin: Palo Alto’s Unit 42 division estimates that 42,000 sites are using Social Warfare, “most of which are running a vulnerable version, including education sites, finance sites and news sites,” it said in an analysis, Monday. “Many of these sites receive high traffic.”
What is linked to with “updated the plugin” tells a different story, since it actually is a link to the plugin’s page on the WordPress Plugin Directory.
The active versions chart on the “Advanced View” page for the plugin on the Plugin Directory shows that only 54.8 percent of websites are using some version of 3.5.x of the plugin:
The vulnerabilities only impact version 3.5.0-3.5.2, so already the figure seems questionable.
Looking at the download chart, which includes anyone updating the plugin, shows that since version 3.5.3 and 3.5.4, which fixed an additional vulnerabilities, there have been tens of thousands of downloads:
So what evidence did Palo Alto’s Unit 42 provide to counter that? None.
Part of that their claim is this:
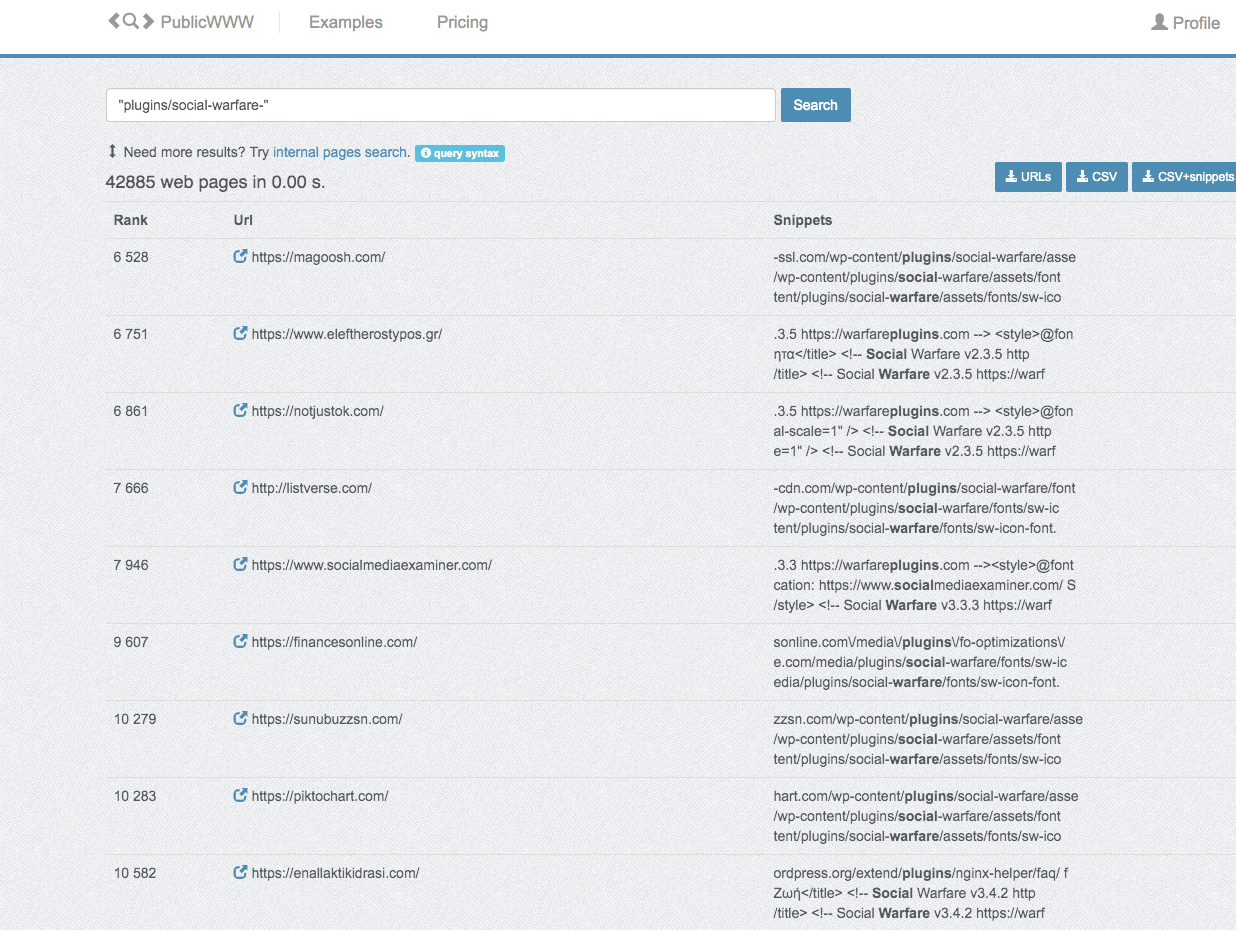
an estimated 42,000 websites are potentially vulnerable until they update to 3.5.3
That links to publicwww.com, which measures how many websites contains reference to “/plugins/social-warfare” in the source of a page, which seems like it will produce a less accurate result then the measure from WordPress. It would seem the people writing that were unaware of the stats provided directly by WordPress, which isn’t a good sign.
As for the claim that “most” websites are running a vulnerable version here is what is written:
We found about 40,000 sites that have installed this plugin, most of which are running a vulnerable version, including education sites, finance sites, and news sites. Many of these sites receive high traffic which we can see with Alexa global traffic rank in the left column in Figure 7:
This is figure 7:
None of those appear to be running a vulnerable version. Some are using a version newer than the vulnerable versions and other are running older versions. That latter element in the best light might explain the claim (though probably not), as their post also claims:
Both vulnerabilities are present in all versions of Social Warfare prior to 3.5.3
That isn’t true at all, they only came in to existence in version 3.5.0. The Threatpost repeated that inaccurate claim.
Nothing else is presented to back the claim that “most of which are running a vulnerable version”.
That post also makes this claim:
In this blog post we provide new details on the root cause of the vulnerabilities, proof of concept code (PoC) to demonstrate the vulnerability, and information on attacks we observed in the wild as well as the scope of vulnerable sites.
Yet the information largely matches what we provided in the first place, which they didn’t link to, and what others already provided. The scope information seems quite wrong.
Considering the freak out we have seen from journalists about us including proof of concepts with our reports on vulnerabilities, it seems strange the Threapost’s article doesn’t address the inclusion of those at all.