Severity Scores From NIST’s National Vulnerability Database (NVD) Are Not Reliable
Two weeks ago, we looked at inaccurate information about claimed vulnerabilities in WordPress plugins, where a journalist was citing information from the National Vulnerability Database (NVD):
The U.S government National Vulnerability Database (NVD) published warnings of vulnerabilities in five WooCommerce WordPress plugins affecting over 135,000 installations.
The NVD is part of the United States Department of Commerce’s National Institute of Standards and Technology (NIST).
As we noted in that piece, the information wasn’t really coming from the NVD, but coming from an unreliable security company. With another organization, CVE, which claims it is sponsored by the US government, being the intermediary between NVD and the security company.
NVD doesn’t make it clear that the information they are publishing is unreliable, despite that being the case. But as we found with another recent situation involving CVE and NVD, NVD is generating their own unreliable information as well.
Two weeks ago we also discussed a claimed “critical” vulnerability in another WordPress plugin, which seems far from that. The security issue would allow someone to have a different IP address than their real one logged in a log of activity done on the website.
As of two weeks ago, NVD was claiming that this vulnerability had a CVSS v3 severity score of 9.8 out of 10, with 10 being the highest score:
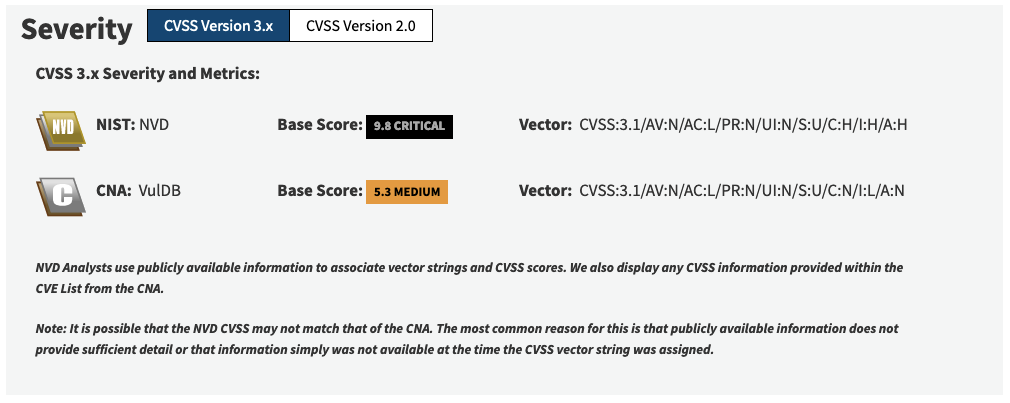
You can also see that the original source of the claim that this was a “critical” vulnerability claimed it only rated 5.3. That rates as “medium”, which conflicts with their claim it was a “critical” vulnerability.
We contacted NVD to let them know that their scoring system seemed broken, using that as an example, and offered to help them replace that with a better system. The response from them was rather troubling, as they didn’t seem to care about whether they are providing accurate information.
While they publish verbatim information from CVE, in the email they claimed they have no idea if the information is legitimate:
The NVD does not participate in the vulnerability disclosure or the CVE publication process, nor are we involved in the determinations for the legitimacy of any particular CVE.
If you look at their entries, they don’t provide a disclaimer warning they don’t know if the information is even legitimate.
While they passed responsibility for that to CVE, CVE doesn’t make sure the information they publish is legitimate either. They instead allow what appears to be just about anyone to publish information through them. If you contact them to let them know that they are publishing falsehoods because of that, they don’t take responsibility for that and instead direct you to contact the entity putting the false information in to their system. NVD falsely claimed that CVE is “constantly working” to improve the system, despite the reality that they are actively doing the opposite:
Members of NIST, the NVD, the CVE Program, vendors/organizations participating in the CVE program and interested third parties are constantly working on ways to improve the systems in place today at scale.
Getting back to NVD, they claimed in their response to us that they don’t actually have any idea if the information they are using to come up with severity scores is accurate and they said they are based on a “worst-case scenario”:
The NVD does not actively perform vulnerability testing, relying on vendors and third-party security researchers to provide information that is then used to assign impact metrics and other attributes. If any information is lacking, unclear or conflicts between sources, the NVD policy is to represent the worst-case scenario.
They don’t provide a disclaimer that makes either of those things clear, here was the disclaimer that was shown instead:
NVD Analysts use publicly available information to associate vector strings and CVSS scores. We also display any CVSS information provided within the CVE List from the CNA.
Note: It is possible that the NVD CVSS may not match that of the CNA. The most common reason for this is that publicly available information does not provide sufficient detail or that information simply was not available at the time the CVSS vector string was assigned.
After our contact with them, they lowered their severity score to 5.3, matching the rating from the security company claiming this was a vulnerability, and still seeming rather high. That is a reduction of 45% points, which shows that NVD scores are not at all reliable, considering they can be off by at least that much.