Patchstack’s Plugin Vulnerability Data Continues to Not Be Impeccable Either
There are many sources for data on WordPress plugin vulnerabilities. Or there appears to be. In reality, most sources are simply copying their data from the others. The results of that are often quite poor, which the providers simply deny. Recently the CEO of Wordfence, Mark Maunder, made this very strong claim about the quality of their (and to a lesser degree, competitor’s) data on vulnerabilities in WordPress plugins:
Our data is impeccable. Our competitors do a pretty darn good job too.
We previously mentioned that, while showing how they had copied inaccurate data from another provider, Patchstack. Where they had incorrectly claimed that an unfixed vulnerability had been fixed. What is the supposed value of telling people that an unfixed vulnerability has been fixed? Data copied the other way shows that there isn’t basic quality control occurring with these data providers.
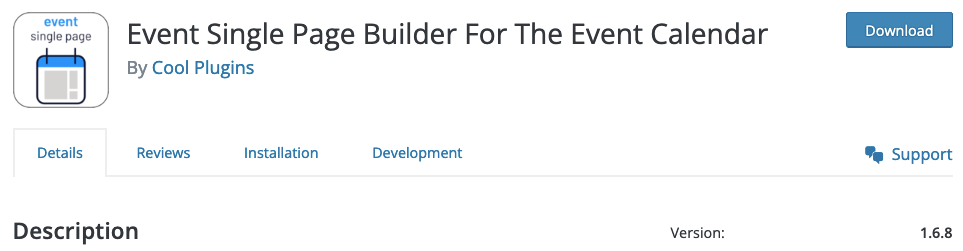
Last week, Patchstack provided these details for a vulnerability they claimed to be in the plugin Event Single Page Builder For The Event Calendar:
Unknown discovered and reported this Sensitive Data Exposure vulnerability in WordPress Event Single Page Templates Addon For The Events Calendar Plugin. This vulnerability has been fixed in version 6.2.8.1.
We noticed that because the developer was being asked about a fix for that.
Something is clearly wrong, as the latest version of the plugin is 1.6.8:
As the developer noted, they were confusing a vulnerability in another plugin from the same developer. The plugin with the vulnerability has 700,000+ installs, and this plugin has 6,000+ installs. It’s unclear how they got that confused. But what they couldn’t have done is to have tested things out, as their source, Wordfence, had not provided basic information needed to check their claim. It is also possible Wordfence may have gotten things wrong, as our testing showed a somewhat different issue than they are claiming had existed.
Patchstack markets their data this way: “Hand curated, verified and enriched vulnerability information by Patchstack security experts.”
It seems highly unlikely that they verified things here, as they didn’t even mention the right plugin, but they also lack a basic sanity check to make sure that the fixed version isn’t higher than the newest version of the plugin. That is something that isn’t hard to implement, as we know, since we have that capability in our system for adding new vulnerabilities to our data set.
Unfortunately, WordPress continues to refuse to warn the WordPress community about the reliable nature of these data sources. Despite the problems it is causing for both users of plugins and the developers of plugins.