Wordfence and “Security News” Outlets Falsely Claim 4 Million WordPress Websites Were Affected by Vulnerability
For reasons we have never understood, various websites portraying them as security news outlets are treated a reliable news outlets, despite not really being news outlets. They are also included in Google News, despite a long history of publishing misleading to outright false claims related to WordPress security. One of those is the Bleeping Computer. In the latest incident related to WordPress, one of their writers, Bill Toulas, wrote a post a titled “Security plugin flaw in millions of WordPress sites gives admin access.” At the end of his post, he gave a more specific figure for the number of websites impacted, 3.5 million:
As of yesterday, the WordPress.org stats site, which monitors installs of the free version of the plugin, showed approximately 450,000 downloads, leaving 3,500,000 sites potentially exposed to the flaw.
The number isn’t close to accurate.
First, the vulnerability was only possible to be exploited if a non-default feature of a plugin was enabled. The writer cited no stats as to how many websites had that feature enabled. Instead, the author said:
The flaw is exploitable when two-factor authentication (2FA) is enabled, and even though it’s disabled by default, many administrators will allow it for stronger account security.
That isn’t journalism. Considering the plugin was until recently focused on SSL, not 2FA, it seems likely that many websites hadn’t enabled it.
More problematic, as the sole source that was cited for the story (where was at least a second source?) claimed, the issue only affected version 9.0 and above of the plugin. That was only released on September 16. So the calculation would be based on assuming that the vast majority of website using the plugins had upgraded since then.
If you look at the stats page cited, you can see that the breakdown of versions used shows that 21.7% of websites are using versions below that:
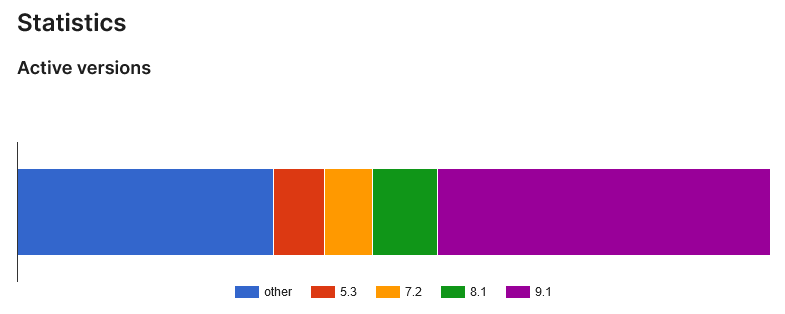
Another 34.1 percent have unspecified versions other than 9.1 and those three other versions. It seems unlikely that many of those would be using version 9.0, considering that 6.7% of websites are using version 5.3, which is two years old.
We don’t know what the real number of website that were actually vulnerable to this, but a more realistic high number would in the hundreds of thousands. That assumes that a large percentage of the website using version 9.0 or above had enabled the non-default feature. A more likely number would probably be tens of thousands. Maybe it was even less than that.
The sole source for that story was Wordfence, which wrote a post titled “4,000,000 WordPress Sites Using Really Simple Security Free and Pro Versions Affected by Critical Authentication Bypass Vulnerability.” That isn’t true, as we already noted. Other “news outlets” were even worse than the Bleeping Computer, as they simply parroted Wordfence’s false claim:
As is usually the case, Wordfence isn’t interested in making WordPress websites more secure, but in promoting themselves as they included this statement near the beginning of the post:
You Can Help by creating as much awareness around this issue in the community as possible, ensuring that any laggard and unmaintained sites update to the patched version.
The update was already forced out by WordPress before their post, but they didn’t emphasize that in the same way. Probably because that would get in the way of using this to promote themselves.
As we will get in to in an upcoming post, there are lessons that can be learned from this situation to improve the security of WordPress websites. Wordfence chose to ignore those.