Automattic’s WPScan Falsely Claims That WordPress Plugin Contained Serious Vulnerability
While reviewing a recent hacker attempt to try to exploit a vulnerability in a WordPress plugin, which was stopped by our own firewall plugin, we found that Automattic’s WPScan had falsely claimed that a WordPress plugin contained a serious vulnerability.
Here was the logging for when the attempt that was stopped:
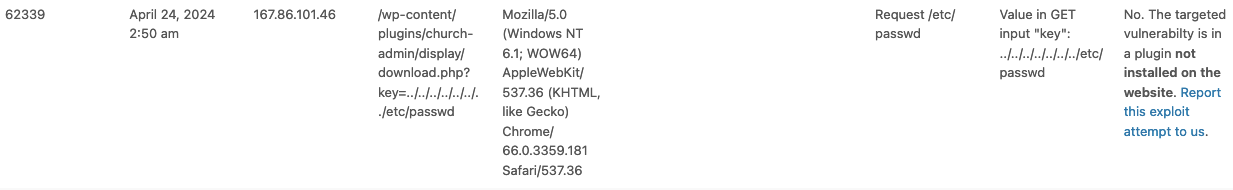
The attacker’s request was trying to view the contents of a file, /etc/passwd, with a request to a file that would come from the WordPress plugin Church Admin:
/wp-content/plugins/church-admin/display/download.php?key=../../../../../../../etc/passwd
We didn’t have an entry for such a vulnerability in our data set, so we set out to figure out if there really was a vulnerability and, if so, add it to our data set.
We found that the data provider, WPScan, which is owned by Automattic, not only claimed the vulnerability existed, but showed a proof of concept matching the exploit attempt that was blocked:

They claimed this was fixed in version 0.565 of the plugin, but not only is there no change made in that version related to that, there also is not even the file that was supposed to contain the exploit. Similarly, the other version mentioned, 0.33.2.1, doesn’t contain the file either.
A vulnerability can’t exist when the file the vulnerability is supposed to be in doesn’t even exist. Clearly WPScan didn’t do basic due diligence. Neither did a hacker, considering the blocked attempt.
Patchstack Too
Another provider, Patchstack, claimed to have provided “early warning” about this non-existent vulnerability:
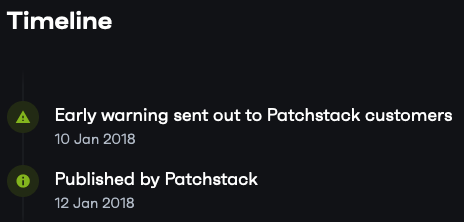
They are claiming that, despite the provider not having even existed at the time and despite claiming to have warned about on the same day WPScan did, so not an early warning.
As this shows, WordPress plugin vulnerability data providers are not all that concerned with accuracy or truthfulness.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade