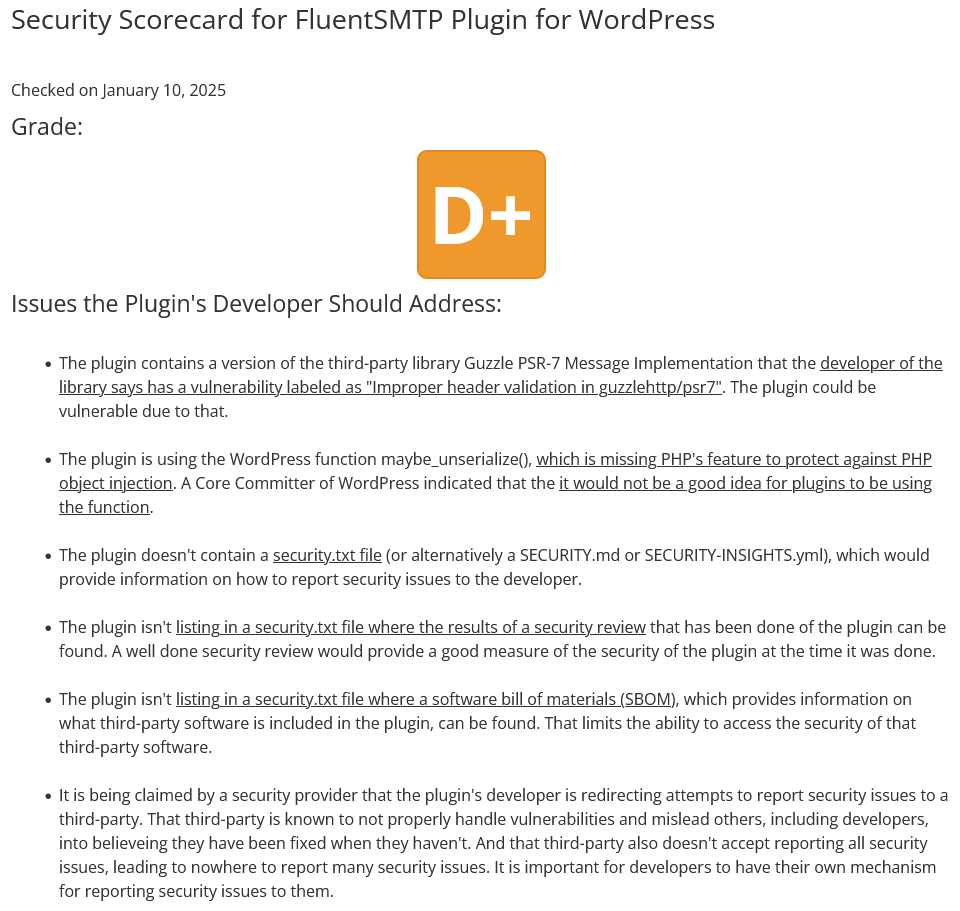
How much do you consider a WordPress plugin developer’s handling of security of their plugins when choosing to use or not use a plugin? Probably not much, considering even if you wanted to, your access to information to make an informed assessment is limited. That is also backed up by the popularity of plugins from developers that have long track records of very public indifference, at best, to security. Depending on the plugin, you have to be worried about not just their handling of security, but the handling of security by developers of third-party libraries that are included in their plugin.
The amount of third-party in some plugins has surprised us. As part of working on our Plugin Security Scorecard since last year, we have been expanding the amount of libraries it can provide information on and warnings when there are publicly known security issues. A few days ago, the security plugin Shield Security was run through the tool again and more libraries were flagged to be included in our data set. There were 5 more libraries in for us to see about adding, that is on top of the 47 that were included in our dataset that are in the plugin. That is a lot of third-party software being included in a plugin originally called WordPress Simple Firewall. [Read more]