WP Tavern’s Justin Tadlock Won’t Address Lack of Due Diligence With False Claims from Patchstack
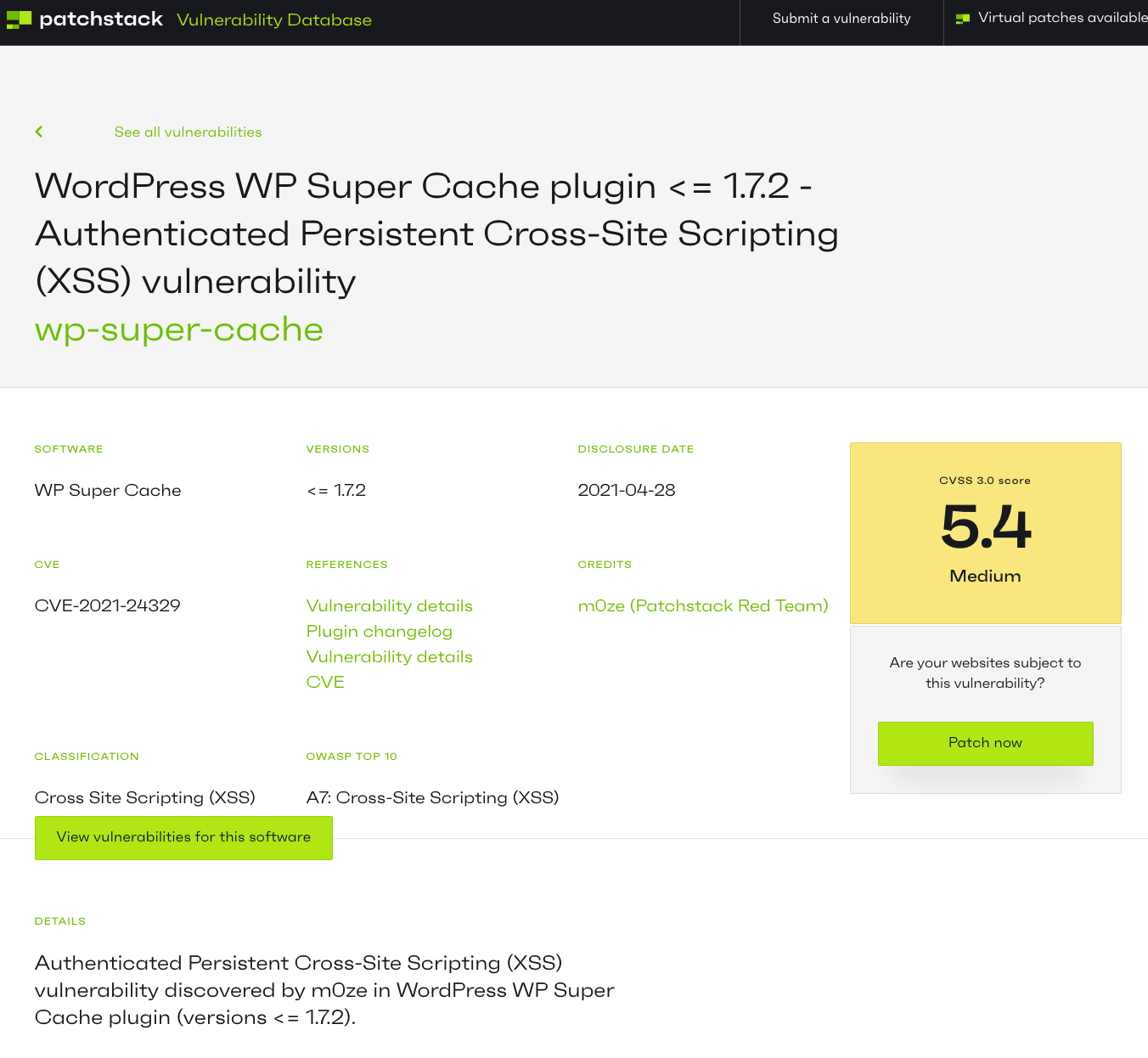
Earlier this year we ran across claims from the web security company Patchstack that a bug bounty program they were running, which they were misleadingly market as a “red team”, was finding an extraordinary amount of vulnerabilities in WordPress plugins.
In May, for example, they claimed that there were 292 vulnerabilities found and that one of the submitter found 149 vulnerabilities and another found 101 vulnerabilities. Both the total and individual numbers sounded hard to believe based on our experience, both collecting up data on vulnerabilities in WordPress plugins and discovering vulnerabilities. [Read more]