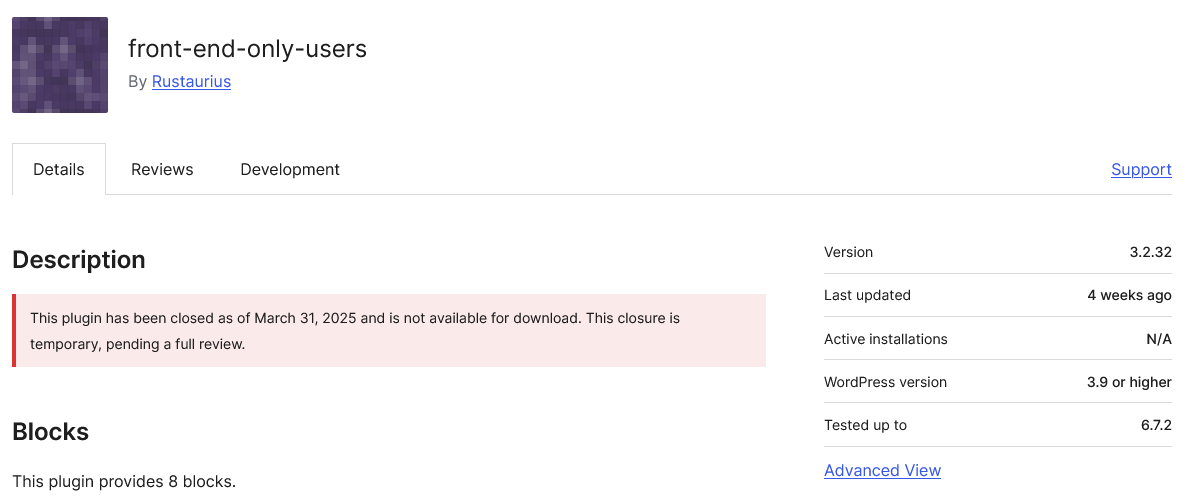
Wordfence’s Unethical Behavior Caused Weeks Long Delay in Fix of Serious Vulnerability
Last week, once again, supposed security journalists and security provider Patchstack were spreading misinformation about a vulnerability in a WordPress plugin. They claimed a vulnerability had been exploited hours after it was disclosed. In reality, there were exploit attempts, but no evidence of any exploitation. And that actually happened a day or a week after the vulnerability was disclosed, depending on what you consider as disclosure.
That a plugin from the developer of the plugin had a vulnerability that would receive interest from hackers isn’t a surprise, as it is a developer that has a long track record of poor handling of security. We recommended not using their plugins in January 2024, unless they could show they had gotten a better handle on security. As we noted in January of this year, they clearly hadn’t gotten a better handle on things by then. With this vulnerability, they did fix it the same day they were informed of it. Unfortunately, the vulnerability was fixed weeks after it should have been, as the notification happened weeks after it should have been. That was because an unethical security provider paid the discoverer to not report it to the developer. [Read more]