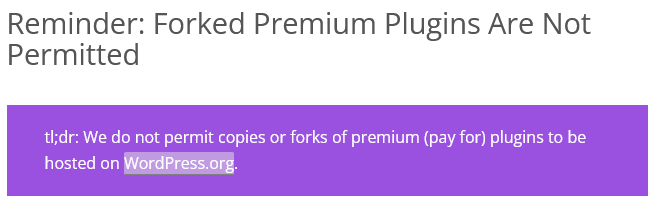
WordPress Plugin Review Team Failing to Enforce Rule, Which is Leading to Popular Plugins Containing Vulnerable Libraries
As part of our work to expand the ability for our Plugin Security Scorecard to identify security issues in WordPress plugins, we have been increasing the number of third-party libraries it can detect being used in WordPress plugins and incorporating information on vulnerabilities the developers have disclosed in those. One place we have been doing that work is during security reviews of plugins. That led to us adding detection for the library jQuery UI to the tool and warning if plugins contain a version that has any of four vulnerabilities disclosed by the developer to have existed in older versions. In recent weeks, we have published several posts that partially focused on WordPress plugins that are using known vulnerable versions of the library. Those situations don’t paint a pretty picture when it comes to plugins usage of third-party libraries.
One of the plugins incorporated a vulnerable version of the library nearly 3 years after it was disclosed by the library’s developer to be vulnerable. [Read more]